If you thought the AI industry deals with big numbers—millions of tokens, giga-zigga-exa-flexa-FLOPs (a very real metric, I tell you)—wait until you hear about the internet. That thing has been taking an absolute beating over the last year. We’ve seen very visible effects of this with various memorable outages, but now we’ve also got some numbers to put to it, in the form of “hyper-volumetric” DDoS attacks.
Giant content delivery network (CDN) Cloudflare has released some somewhat troubling stats and info regarding the past year of distributed denial of service (DDoS) attacks. These are essentially attacks that attempt to flood a target service with packets of data to overload and overwhelm it and prevent it from doing the work it’s actually meant to be doing, such as providing an internet connection to customers or displaying webpages.
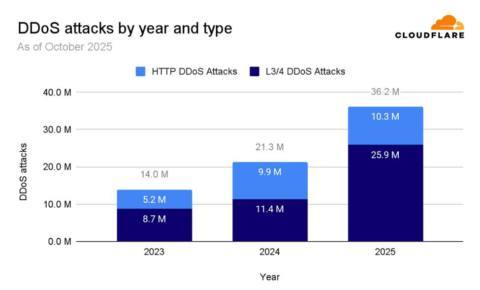
According to Cloudflare, DDoS attacks are up 170% to 36.2 million in 2025 compared to 2024. To zoom in a little, the company says that in the third quarter of 2025, it “mitigated an average of 3,780 DDoS attacks every hour.” That’s 63 DDoS attacks each minute, or about one every second.
Not every DDoS attack is a noteworthy one, of course, but there have been a few noteworthy ones over the past few months. In particular, a few were highlighted by Cloudflare over the last couple of months as consecutive record breakers (woo?).
In the weeks leading up to September there was a DDoS attack that attempted to flood its target with 11.5 Tbps of data. Then, in late September, there was one that topped this with an attempt to flood its target with 22.2 Tbps of data, which equated to 10.6 billion packets of data per second. And then there was one in early October that saw a new record 29.6 Tbps flung at its target. These attacks each lasted less than a minute.
Those small timeframes are a real problem if you don’t have automated defenses in place: “most attacks, 71% of HTTP DDoS and 89% of network-layer, end in under 10 minutes. That’s too fast for any human or on-demand service to react. A short attack may only last a few seconds, but the disruption it causes can be severe, and recovery takes far longer.”
We’ve seen how long it can take for simple mistakes to be cleaned up and service to be restored. Cloudflare’s recent outage, for instance, was caused by a double-sized file propagating throughout the network. This likely happened quite quickly, but it took hours for service to be restored to full, normal functionality.
To simplify probably far too much, DDoS attacks are generally defended by figuring out which packets of data coming in are illegitimate and then simply not processing them. Cloudflare’s defenses seem to have done a good job at this, given these big attacks were defended.

But as Cloudflare’s quarterly and yearly stats show, the number and the scale of these attacks seems to be exponentially increasing. According to Krebs on Security, linked previously, the Aisuru botnet responsible for the latest record-breaking DDoS attack apparently caused widespread internet disruption in the US simply due to attempted DDoSing, that’s all without the attack succeeding.
A botnet, if you weren’t aware, is like a hivemind of connected computers that are usually connected together unbeknownst to their users. All the systems can, at the behest of the attacker(s) in control of the botnet, be prompted to dish out some packets of data that, when combined with all the packets from other computers in the secret network, makes for a giant mass. A mass that barrages a target with, say, 29.6 terabytes per second of data. In “distributed” fashion, ergo, “distributed denial of service.”
In other words, lovely stuff to help us sleep at night. It does make me hope my PC isn’t some kind of sleeper agent. I’ll keep my side-eye firmly planted on its suspiciously unassuming chassis, just in case.






